All the Cisco switches has two operational modes
− User Exec Mode :
When a user first establishes the connection with the
switch, and enter the password, the switch is in ‘User
EXEC Mode’, and the prompt is ‘>’.
− Privileged Mode: when user enter the command ‘enable’ and supply the password, it enters the privileged mode, and the prompt is ‘#’
− Only in privileged mode, a user can enter configuration mode; to enter configuration mode, user must enter the command ‘config t’
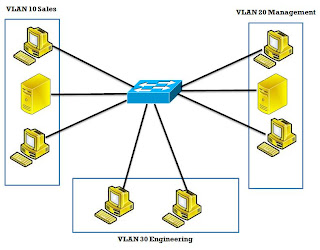
A virtual LAN (VLAN) is a logical LAN, or a logical subnet.Vlan defines a broadcast domain. A physical subnet is a group of devices that shares the same physical wire. A logical subnet is a group of switch ports assigned to the same VLAN.
· Logically divide a switch into multiple, independent switches at L2· Create separate broadcast domains in a switch, increasing the number of broadcast domains· Span multiple switches using trunks
· Allow logical grouping of users by function
· Simplify adding, moving, and changing hosts in the network
· Enhance security
· Logically divide a switch into multiple, independent switches at L2· Create separate broadcast domains in a switch, increasing the number of broadcast domains· Span multiple switches using trunks
· Allow logical grouping of users by function
· Simplify adding, moving, and changing hosts in the network
· Enhance security
 VLAN configuration steps:1. The VLAN must be created.
VLAN configuration steps:1. The VLAN must be created.2. The VLAN may be named.
3. The desired ports must be added to the new VLAN.
Note: Routing between VLANs requires a router or Layer 3 switch.
Creating Static VLANs
There are 2 ways of create Vlans:
• Using the VLAN configuration mode, which is the recommended way to create VLANs
• Using the VLAN database mode (which should not be used but is still available)